Cloudflare Access

Today I discovered a straightforward method to secure a self-hosted website using Cloudflare Access, assuming the DNS is managed through Cloudflare and Cloudflare Tunnel is in use.
I've been hosting Teslamate on a local server with Docker, but recently moved it to GCP, utilizing a free E2 micro-instance. For this transition, I used my tool, CloudTailor, to install and deploy the teslamate/teslamate:latest Docker image.
I modified the Terraform files produced by CloudTailor before deployment, ensuring the Docker-Compose.yml file aligned with Teslamate documentation. Additionally, I updated the setup_cloudflare.sh script to enable Cloudflare Tunnel to support subdomains for both Teslamate and Grafana. After deploying the Terraform files and setting up the VM, I SSH'd into it and executed the setup_server.sh and setup_cloudflare.sh scripts in the /opt directory, then followed the Teslamate Usage instructions to configure the apps.
As a macOS user, I utilized the Auth App for Tesla to create tokens for accessing my Teslamate setup. A challenge I faced was the lack of default password protection in Teslamate. Since I was using Cloudflare Tunnel with SSL, I needed a simple solution for password protection.
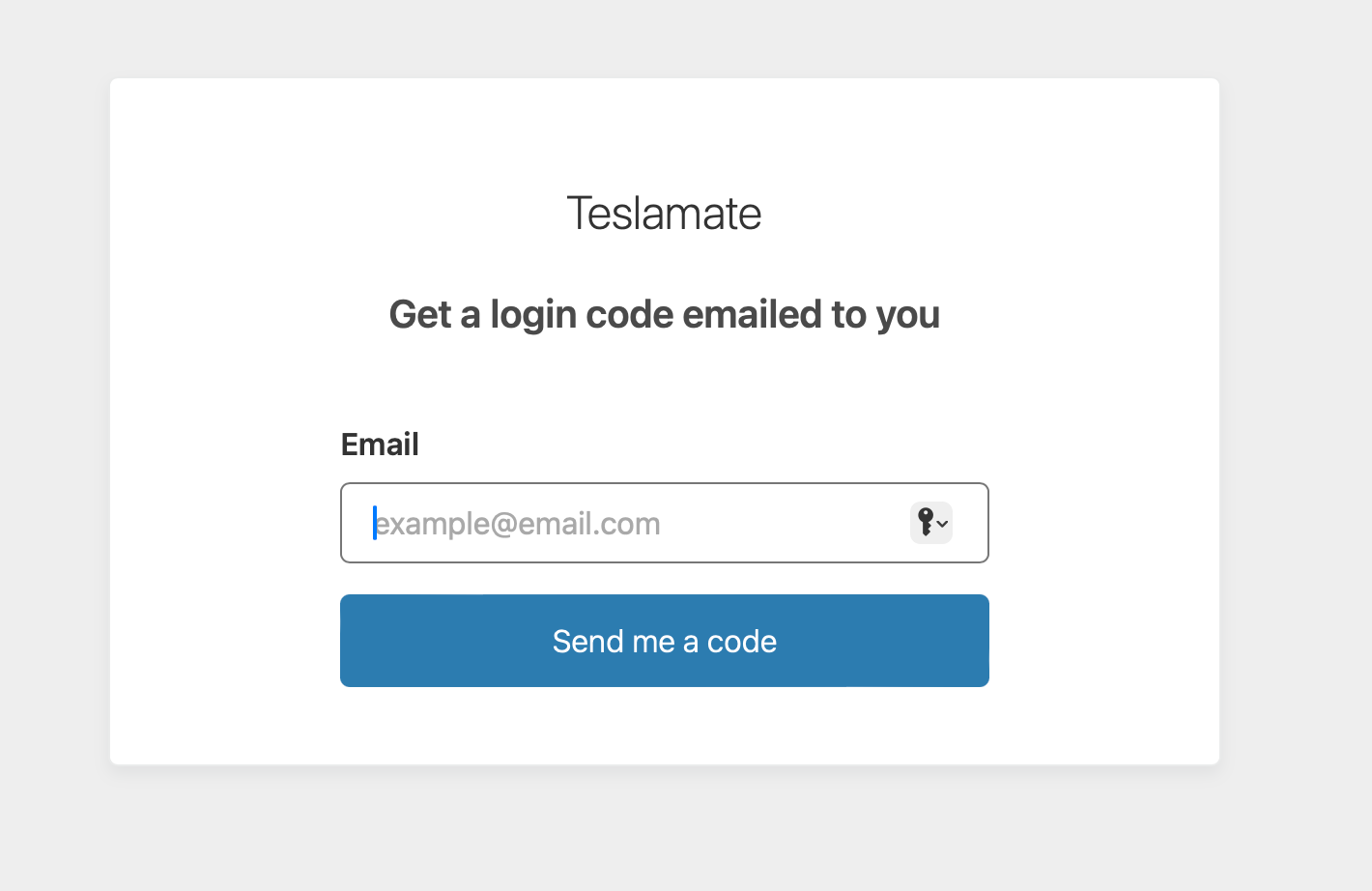
This led me to Cloudflare Access, which I learned today offers an easy way to protect self-hosted applications with Zero Trust policies. Through the Cloudflare dashboard, I navigated to Zero Trust > Access > Applications and added an application. I set up my self-hosted Teslamate domain for protection and configured access to be limited to specific Google accounts. For authentication, I chose to only allow a few Gmail addresses. The settings I configured below provide a nice low headache solution. In the configuration shown below only the user allowed@gmail.com is able to access Teslamate by first retrieving a code sent to them. Handy in a pinch!
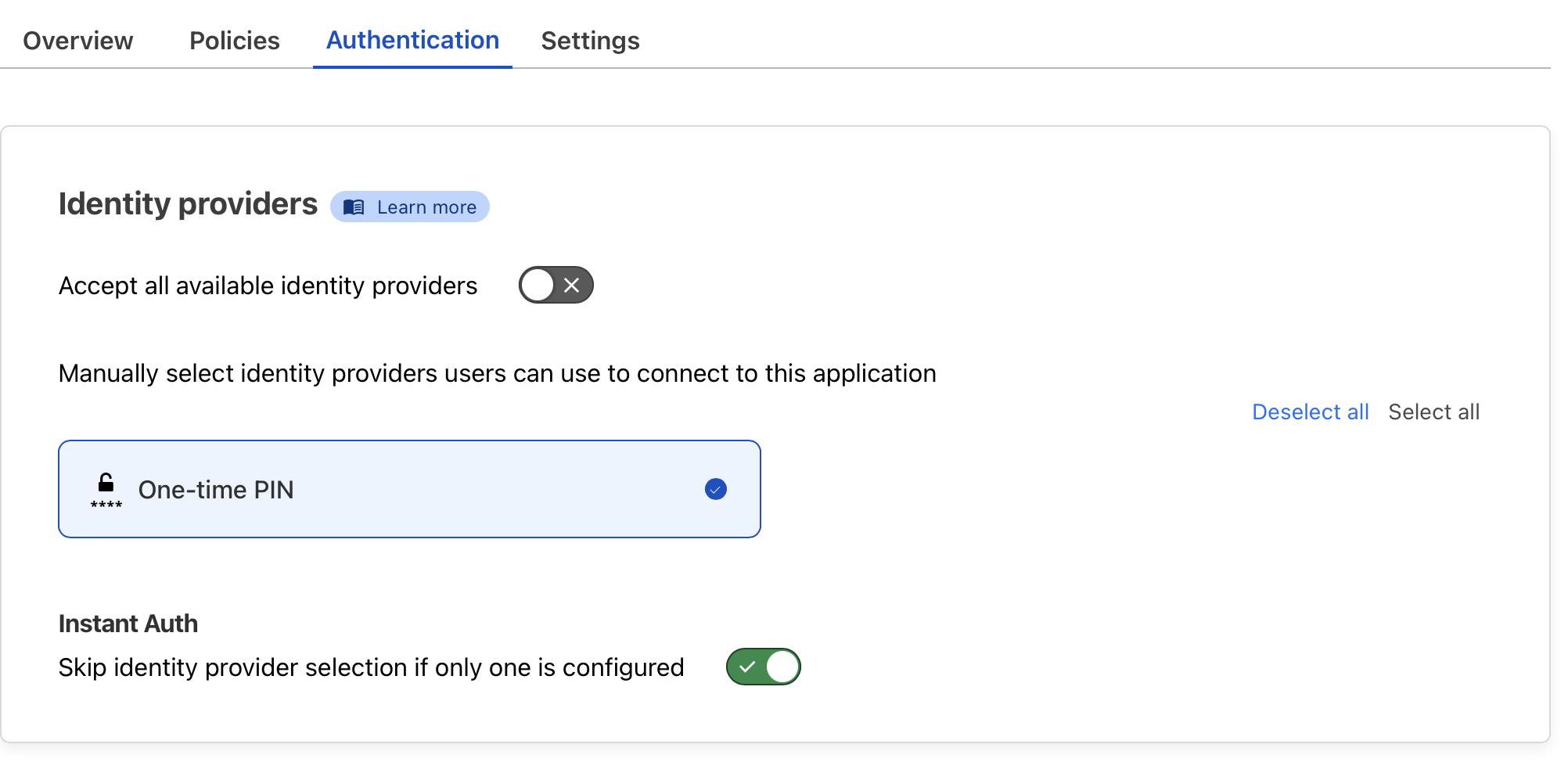
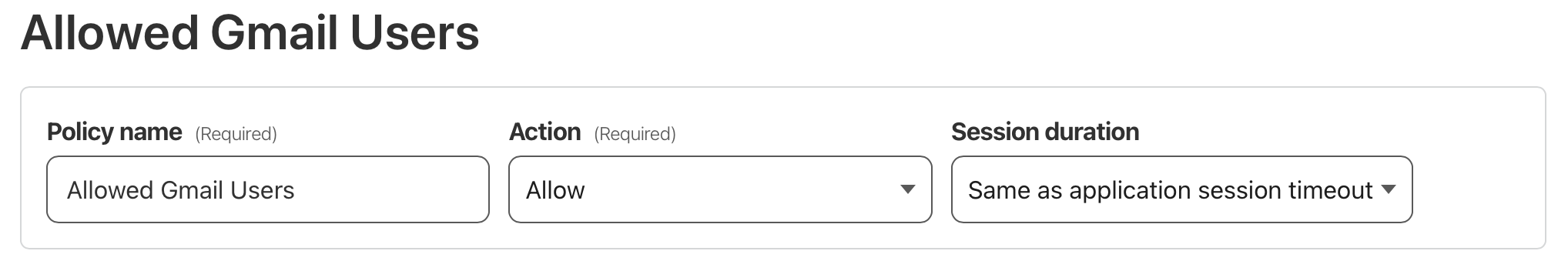
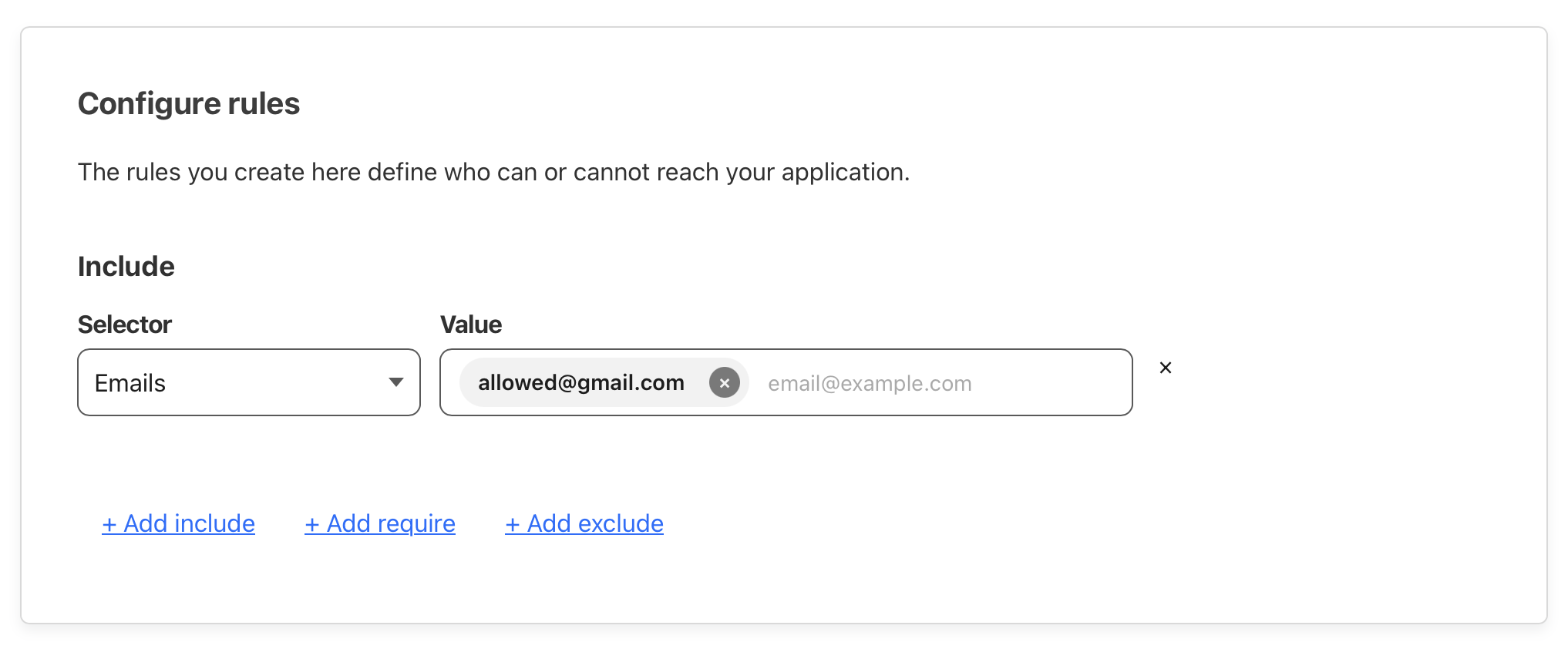
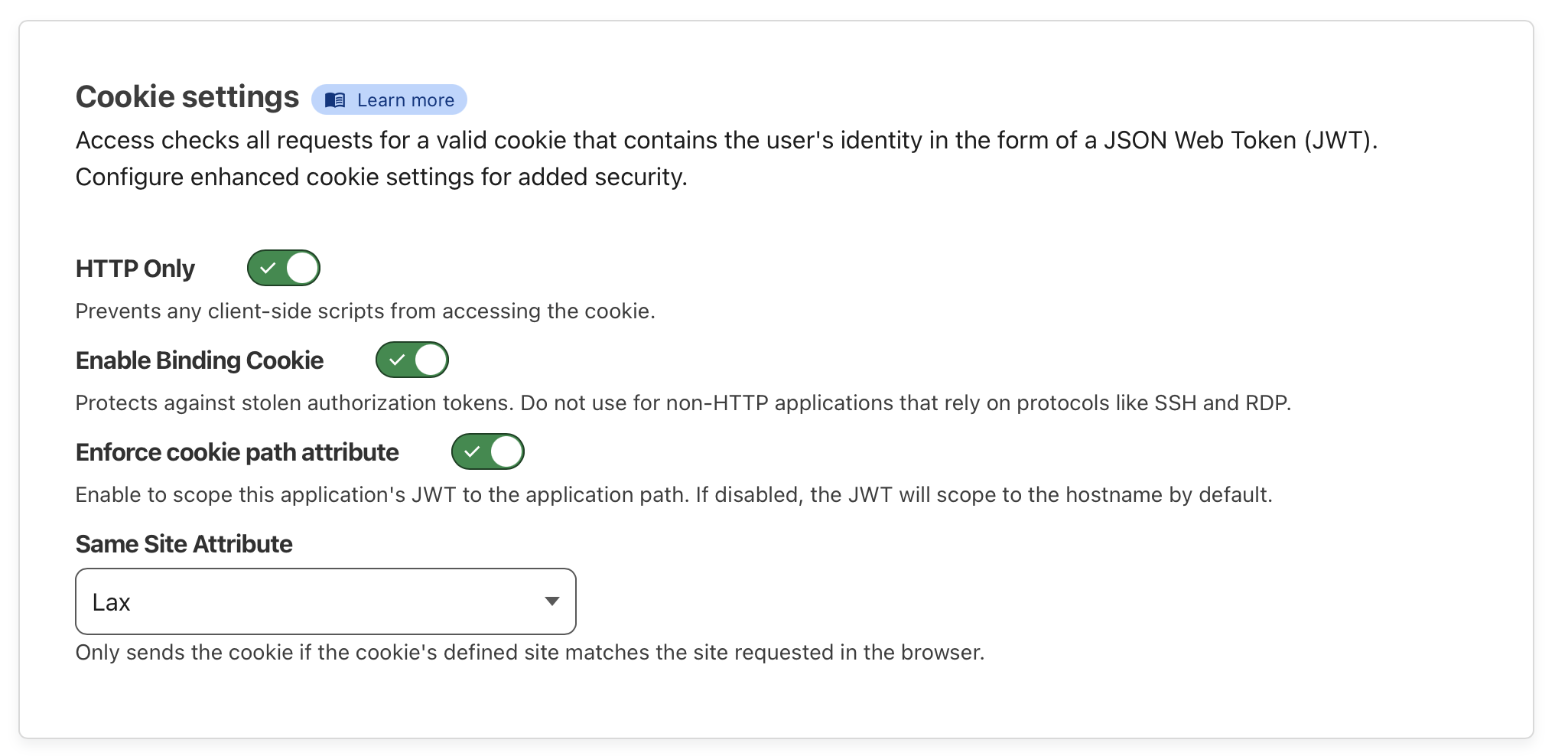
My self-hosted Teslamate site is now protected when visited and only the allowed email addresses that were configured will get a code sent to them.